Recovering keys with MFKey32

If you couldn't read all the MIFARE Classic® card's sectors with the Read function or the sectors you read aren't enough to get access, try to use the Detect Reader function. The Detect Reader function performs the MFKey32 attack, which exploits weaknesses in the Crypto-1 encryption algorithm. MFKey32 is the name of a tool/algorithm to recover the MIFARE Classic keys from the reader’s Crypto-1 nonce pairs. It works by recovering the initial state of the Crypto-1 Linear Feedback Shift Register, which contains the key.
On this page, you'll learn how to conduct the MFKey32 attack if you have access to the card and what you can do if you don’t have access to the card.
The best way to conduct the MFKey32 attack is to have access to the card, even if not all sectors were read. By getting the reader's key, you can read more sectors of the card, which might be enough to open the door.
To get the reader's keys and read the MIFARE Classic card, do the following:
Read and save the card with your Flipper Zero.
Go to Main Menu -> NFC -> Saved -> Name of the saved card -> Detect reader. Flipper Zero will emulate this card for the MFKey32 attack.

Tap the reader with your Flipper Zero, as shown below. When near the reader, your Flipper Zero will collect the reader's nonces. Depending on the reader, you may need to tap the reader with your Flipper Zero up to 10 times in order to simulate several card authentications. On your Flipper Zero's screen, the number of collected nonce pairs should increase with each new tap of the reader. If the number of nonce pairs doesn't increase, the reader is not trying to authenticate the card emulated by your Flipper Zero.

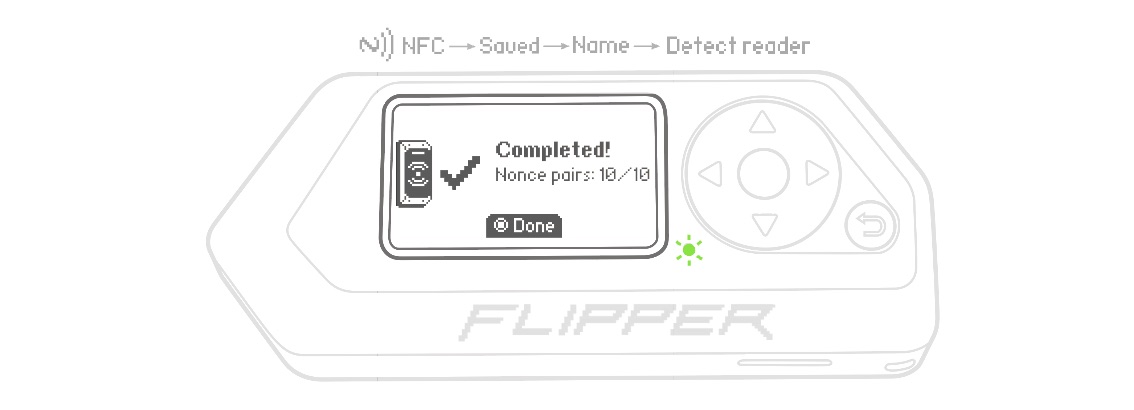
Press %ok%OK to save the collected nonce pairs to the microSD card. Once the required number of nonce pairs is collected, the screen will display a Completed message. After that, you can press the %ok%OK button to view the captured data, including the sector and key from which it was obtained.

Recover keys from the collected nonces. You can do it via: Flipper Mobile App
- Go to Hub -> NFC tools -> Mfkey32 (Detect Reader).
Flipper Lab
- Connect your Flipper Zero to your computer via a USB-C cable.
- Go to NFC tools, then click the GIVE ME THE KEYS button.
Mfkey32 app
If you don't have access to a smartphone or computer, you can recover keys from the collected nonces using only your Flipper Zero. Keep in mind that it takes several minutes to recover the keys due to the limited computing power of the device.
- On your Flipper Zero, go to Main Menu -> Apps -> NFC.
- Run the Mfkey32 app and press the %ok%OK button.
The recovered keys will be displayed on the screen. After that, they can be added to the User dictionary. In some cases, the keys can’t be recovered from the nonces due to the reader not recognizing your Flipper Zero’s emulation properly.
Once new keys are added to the User dictionary, read the card again. The number of found keys and read sectors may increase, which indicates that necessary data is collected.
Emulate the card and hold your Flipper Zero near the reader to get access.

Even if you don't have access to the card, you can try to get the reader's keys and then add them to the User dictionary to expand it.
To get and save the reader's keys, do the following:
Go to Main Menu -> NFC -> Detect reader. Flipper Zero will emulate an NFC card for the MFKey32 attack.

Tap the reader with your Flipper Zero as shown below. When near the reader, your Flipper Zero will collect the reader's nonces. Depending on the reader, you may need to tap the reader with your Flipper Zero up to 10 times in order to simulate several card authentications. On your Flipper Zero's screen, the number of collected nonce pairs should increase with each new tap of the reader. If the number of nonce pairs doesn't increase, the reader is not trying to authenticate the card emulated by your Flipper Zero.

Press %ok%OK to save the collected nonce pairs to the microSD card. Once the required number of nonce pairs is collected, the screen will display a Completed message. After that, you can press the %ok%OK button to view the captured data, including the sector and key from which it was obtained.
Recover keys from the collected nonces. You can do it via: Flipper Mobile App
- Go to Hub -> NFC tools -> Mfkey32 (Detect Reader).
Flipper Lab
- Connect your Flipper Zero to your computer via a USB-C cable.
- Go to NFC tools, then click the GIVE ME THE KEYS button.
Mfkey32 app
If you don't have access to a smartphone or computer, you can recover keys from the collected nonces using only your Flipper Zero. Keep in mind that it takes several minutes to recover the keys due to the limited computing power of the device.
- On your Flipper Zero, go to Main Menu -> Apps -> NFC.
- Run the Mfkey32 app and press the %ok%OK button.
The recovered keys and sector numbers will be displayed on the screen. After that, they can be added to the User dictionary. In some cases, the keys can’t be recovered from the nonces due to the reader not recognizing your Flipper Zero’s emulation properly.
MIFARE and MIFARE Classic are registered trademarks of NXP B.V.
